Understand Azure Security Before you Regret
Security in Azure
Migration from the customer-controlled on-premise data center to cloud-based datacenters like Azure shifts the responsibility for security. Many customers tend to think that security is completely outsourced to the cloud vendor. Well, It’s not!
Security is a shared responsibility. Below is a comparable category of different cloud deployment models and on-premise, only with respect to Security.
| Responsibility | On-Premises | IaaS | PaaS | SaaS |
| Data governance and Rights Management | Customer | Customer | Customer | Customer |
| Client endpoints | Customer | Customer | Customer | Customer |
| Account and access management | Customer | Customer | Customer | Customer |
| Identity and directory infrastructure | Customer | Customer | Microsoft/ Customer | Microsoft/ Customer |
| Application | Customer | Customer | Microsoft/ Customer | Microsoft |
| Network controls | Customer | Customer | Microsoft/ Customer | Microsoft |
| Operating system | Customer | Customer | Microsoft | Microsoft |
| Physical hosts | Customer | Microsoft | Microsoft | Microsoft |
| Physical network | Customer | Microsoft | Microsoft | Microsoft |
| Physical datacenter | Customer | Microsoft | Microsoft | Microsoft |
There is a layered approach to security in multiple steps. Here are some of the layers with Azure services.
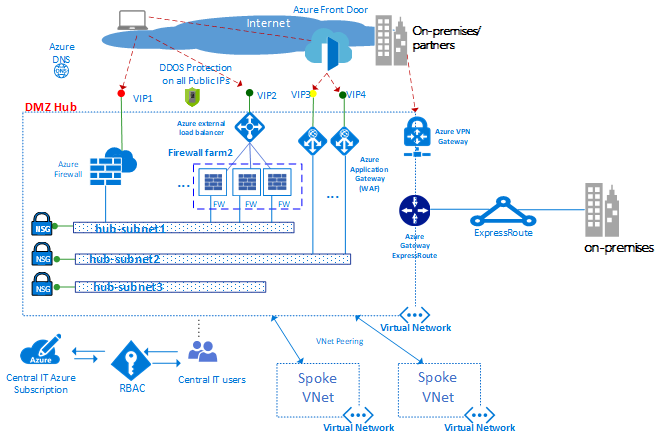
Perimeter Layer
The perimeter layer protects your network boundaries. Azure DDOS Protection & Azure firewall can be applied on VNet (network boundary) during the deployment.
Network Layer
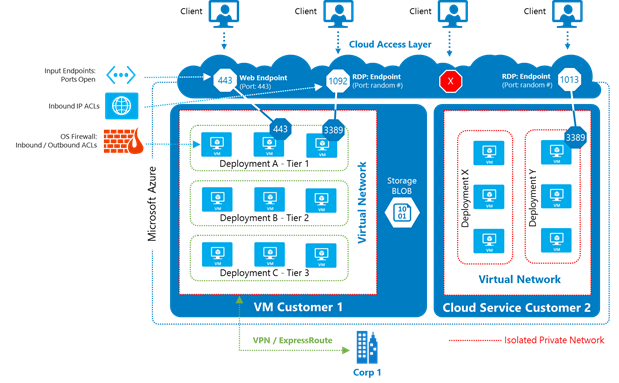
Permits traffic between network resources based on inbound & outbound ruled. Azure NSG is a service for this layer that works on 5-tuple hash which is source IP, destination IP, source port, destination port & protocol.
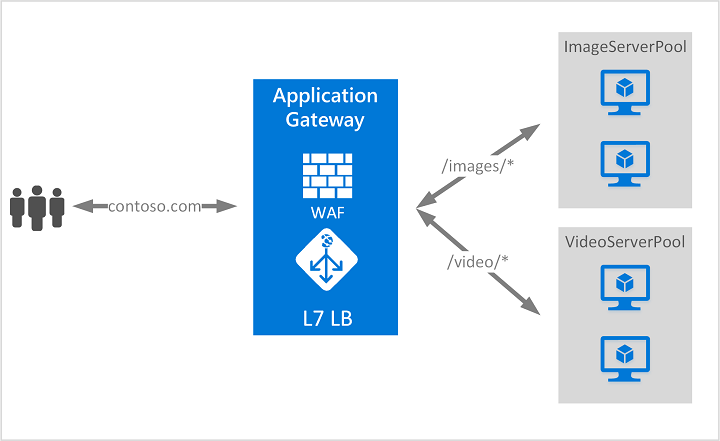
Application Layer
The application security group provides a grouping of servers with similar port filtering requirements. We can also add group servers based on functionality such as web servers, application servers, etc.
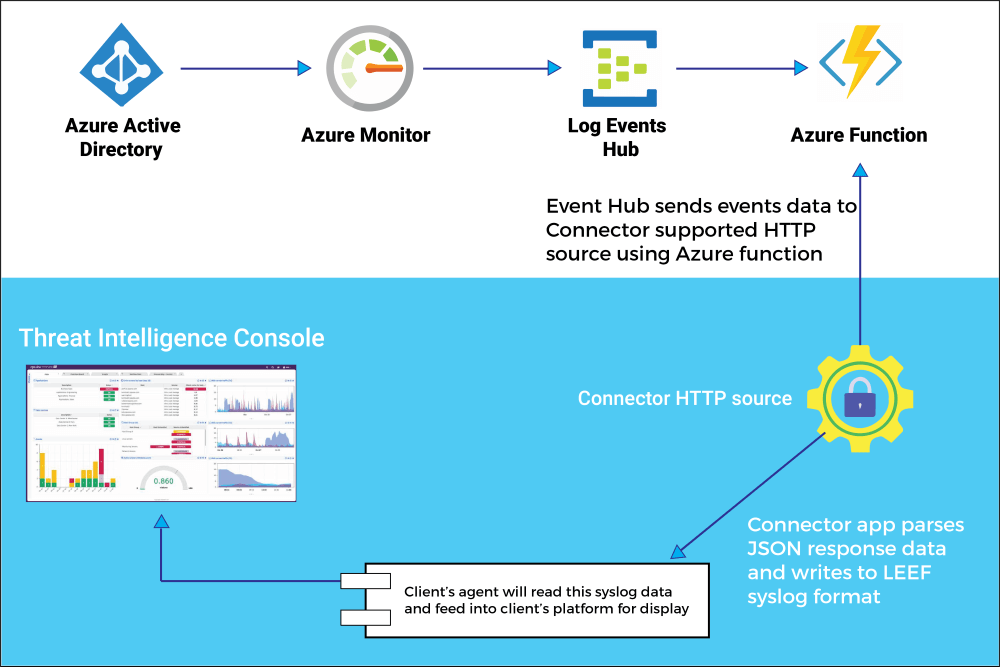
Detect threats early with unique intelligence
Identify new threats and respond quickly with services that are informed by real-time global cybersecurity intelligence delivered at cloud scale. These actionable insights are developed by analyzing vast sources including 18 billion Bing web pages, 400 billion emails, 1 billion Windows device updates, and 450 billion monthly authentications.
Using machine learning, behavioral analytics, and application-based intelligence, data scientists analyze the flood of data in the Intelligent Security Graph. The resulting insights inform services in Azure and help you detect threats faster.
Security is a shared concern between customer & cloud vendor!
For any consulting requirements, please email us on cloud@proarch.com